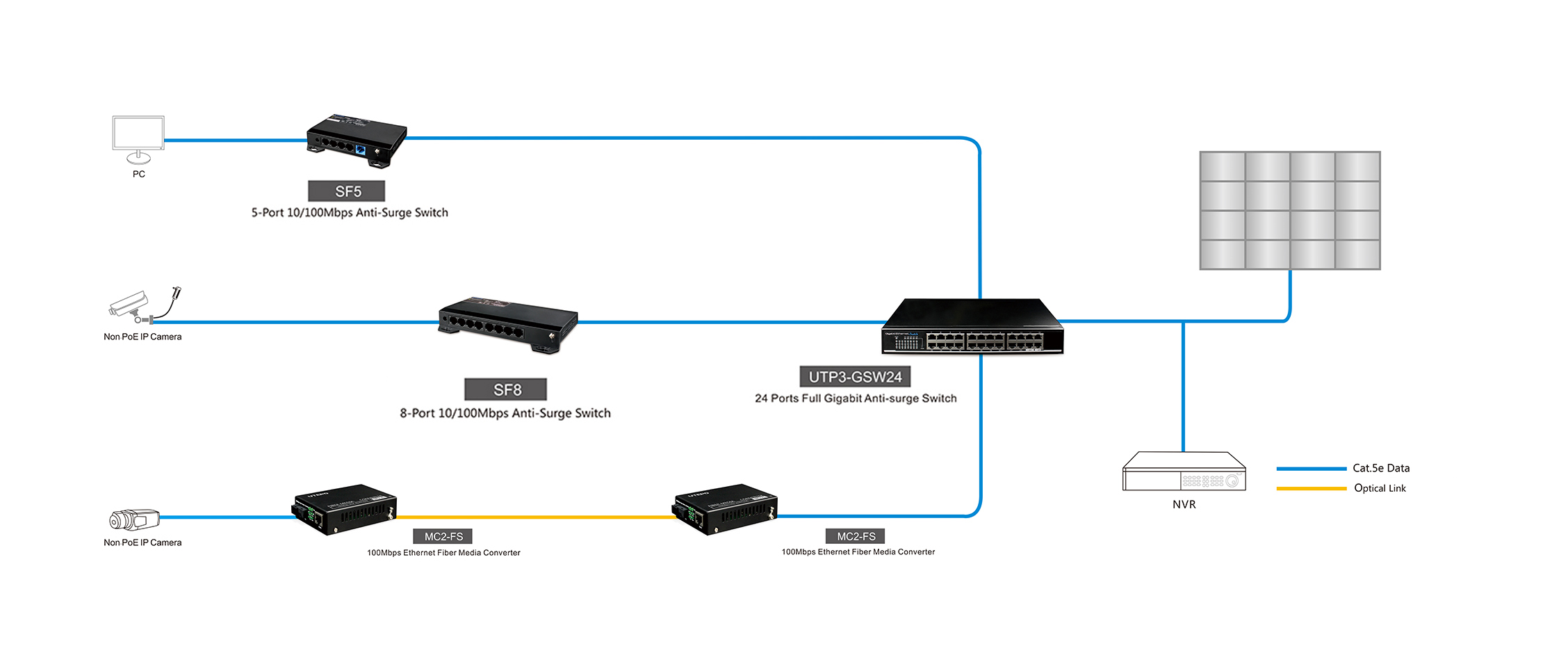
The Internet is an inseparable part in people’s life nowadays, especially in the informatization of enterprise, in which it contains not only a completed office information system, but also builds a video surveillance system.
However, due to the lack of an overall planning or the ill-considered selection of network products, it fails to deliver the desired result in network construction, and causes a lot of problems subsequently.
Here are some common problems in applications:
POOR SPEED OF NETWORK CLONE
Network clone is using a sever to transit data to several clients simultaneously in an LAN through multicast or broadcast, with the purpose of auto-install, update or restore for the system in client.
Sometimes, the speed of the network clone on the switch would be low in diskless system or PCI of Internet cafe or campus network. It could get the network clone back to normal work through changing the function setting of storm control & flow control etc., such as disable the flow control of all ports.
In general, it requires the parameter setting in the WEB management or coding to modify the switch configuration, which is difficult and gains a lot of works to network administrators due to the different setup of each brand switch.
NETWORK PARALYSIS CAUSED BY SWITCHING LOOP
With the expansion of network scale in campus, community, hotel and small and medium sized enterprise, it needs to newly connect a large amount of switches into the network, if not familiar with the network structure, it would easily cause the switching loop.
A switching loop occurrence would lead to the repeatedly rebroadcast messages, thus, the resultant broadcast storm will greatly occupy network resources as well as the failure of forwarding the packets. Seriously, it may influence the quality of network and cause the network paralysis.
- Occurrence Reasons:
There is more than one Layer 2 (OSI model) path between two endpoints (e.g. multiple connections between two network switches or two ports on the same switch connected to each other). It is easy to cause the switching loop when newly add device into the network or expand the network, such as adding the network for a new department.
- Influence:
The loop creates broadcast storms as broadcasts and multicasts are forwarded by switches out every port, the switch or switches will repeatedly rebroadcast the broadcast messages flooding the network, therefore the network would react very slowly. The most direct symptom is to affect network of the same VLAN users, there will be an unstable situation of network.
Due to the wrong wiring in the network is prone to cause the loop, UTP3-GSW16/24 can timely and effectively detect whether there is a loop in the network without any configuration, automatically block the port, and improve the network reliability.
IP ADDRESS CONFLICT CAUSED BY UNAUTHORIZED SOHO ROUTER
Many enterprise users often encounter such a situation, the network is good, suddenly they can not get access to the network or the network becomes slow.
After checking the network configuration, they found that the performance and port of the switches were all good. But when input the IP address of router to login, they found that the router was the unauthorized SOHO router, which was connected privately by other departments or other personnel. The SOHO router caused the IP address conflict and influenced the network.
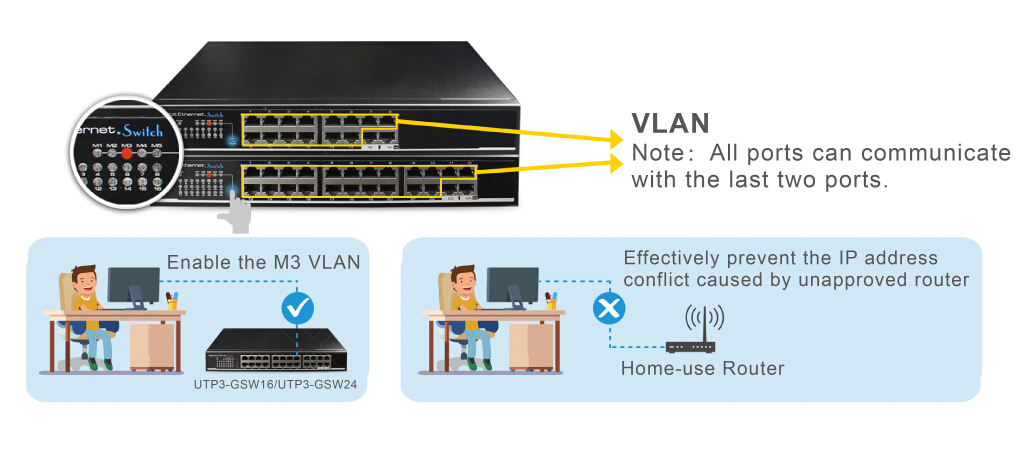
This situation often happens in enterprises with many departments, personnel dormitory or hotel. Take hotels as an example, customers often connect their wireless router to the hotel network, resulting in IP address conflict and network crash.
In order to avoid above situation, it needs to configure the DHCP snooping for the switch and isolate the ports. However, it requires the knowledge of network and code for the system setting, which increases the workload.
THE LAN WAS ATTACKED BY ARP VIRUS
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address that is recognized in the local network.
Due to the design defects of ARP, the hacker will change the corresponding relationship between IP and MAC, and illegally obtain and replace other people's MAC to illegally get data information.
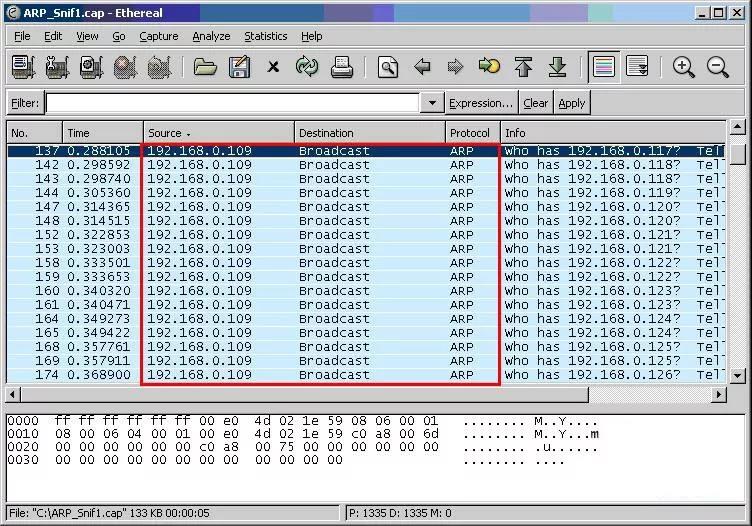
ARP spoofing attack is a very common network phenomenon, while many users use switch to prevent ARP attack. For example, by configuring the maximum number of MAC addresses on a port, limiting and binding MAC addresses prevents users from performing malicious ARP spoofing, but this setup is also complex.
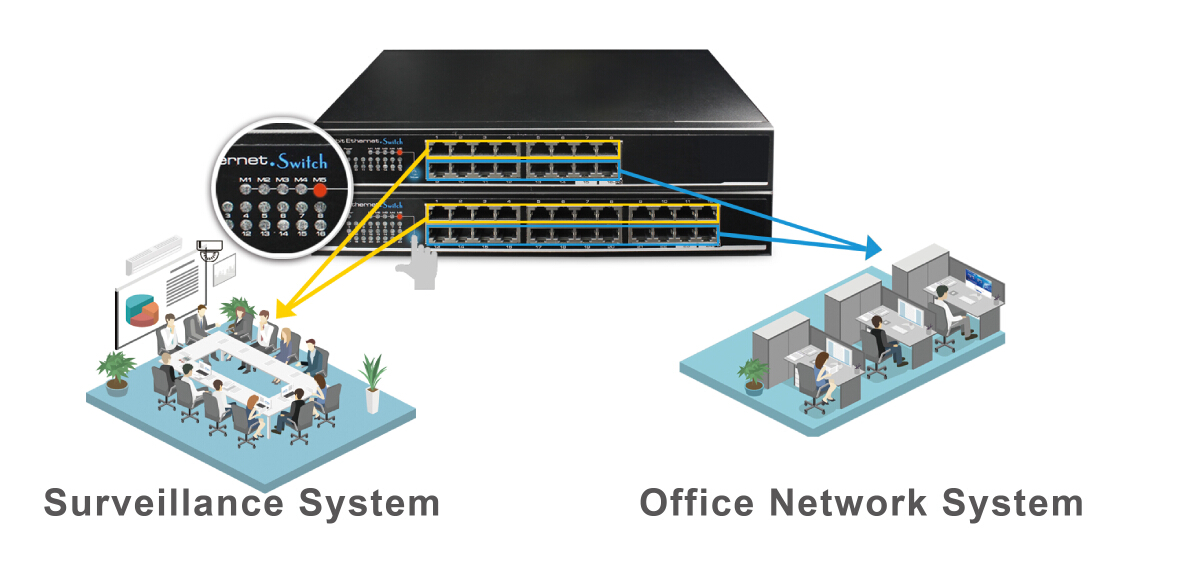
SLOW OFFICE NETWORK CAUSED BY OVER OCCUPIED OF MONITORING DATA
With the application of video monitoring system gradually popularized, it is widely used in enterprise information construction. At the beginning of planning the information system, many enterprises fail to effectively isolate the office network from the monitoring network, resulting in a large bandwidth of video monitoring data and a slow office network speed, which affects the normal business development of enterprises.
Generally, network administrators will isolate the ports through VLAN or use independent switches to isolate the office network and monitoring network. Considering the limited budget, some achieve the goal of network isolation by setting up different network segments. Of course, the network application problem in different application scenarios is much more than these. However, if the network planning can be done in advance, or do a good job in equipment selection and configuration, can greatly reduce the network fault.
To ensure network security and the stability of network applications, the selection and configuration of switches are quite critical. But the network equipment setting is quite tedious, even to the specialized technical personnel, it also unavoidably will meet some difficult problems.
Is there any a switch that can not only provide different network security solutions for different application scenarios and network environments, but also can switch to the expected application mode with one key according to the application scenarios without complicated settings?
In view of the current network construction and application pain points, combining with the small and medium-sized enterprises gigabit networking and monitoring networking application characteristics, UTEPO had launched the 16/24 ports full gigabit anti-surge engineering exclusive Ethernet switch.
Equipped with the unique 5 operating modes, including STANDARD, SAG&LP, VLAN, LOCK, ISOL, the switches ensure the reliability of data transmission and are widely used in security video monitoring and network engineering etc.
- M1(STANDARD): Disable flow control of all ports, which is suitable for low-speed & non-disk networking such as cloud course & cloud desktop.
- M2(SAG & LP): All ports support automatic detection and block for loop links, and the last two ports could be an aggregation group The mode is suitable to engineering fields such as video monitoring, requiring high bandwidth and reliability.
- M3(VLAN): Port 1 to 14 are isolated respectively, but can communicate with Port 15-16, preventing the system from IP address conflict.
- M4(LOCK): Limit MAC learning (only single address is allowed to single port) and mark the port with 'lock' status, preventing the ARP attack.
- M5(ISOL): Isolation between Port 1-8 and Port 9 16, which can be used for isolation of monitoring system and office network, to ensure the security of network data.
+86-755-83898016-863
+86-1501-2669-765
[email protected]
Note: To speed up our service to you, please make sure the field with " * " mark is filled before you click on "Submit" button, Thank you!