VLAN is any broadcast domain that is partitioned and isolated in a computer network at the OSI data link layer. It is a logical overlay network that groups together a subset of devices that share a physical LAN, isolating the traffic for each group.
In this article, we'll discuss the followings.
* Why need VLAN?
* VLAN vs. Subnet
* VLAN Tagging & VLAN ID
* Processing mechanisms on interface type and tag of VLAN
* Application of VLAN
* Protocols related to VLAN
* Problems with VLAN in cloud-based scenarios
Why need VLAN?
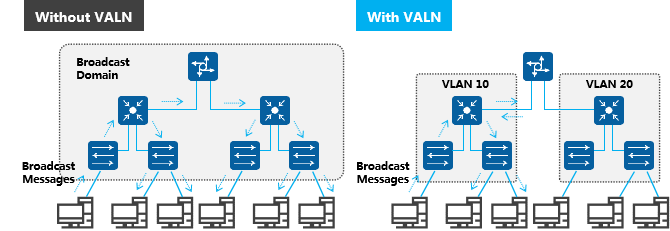
Traditional Ethernet is a data network communication technology based on CSMA/CD (Carrier Sense Multiple Access/Collision Detection) shared communication medium. When the number of hosts is large, it leads to conflicts, broadcast flooding, significant performance degradation, and even network unavailability. Although LAN interconnection through Layer 2 devices can solve the problem of the conflicts, it still cannot isolate broadcast messages and improve network quality.
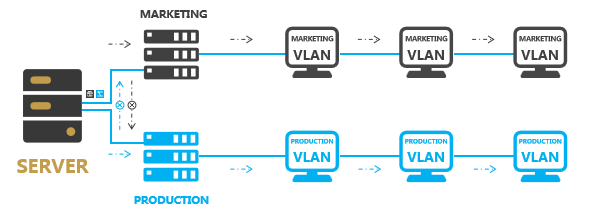
In this case, VLAN technology emerged. This technology can divide a LAN into multiple logical VLANs, and each VLAN is a broadcast domain. Hosts within a VLAN intercommunicate while cannot communicate with the hosts directly in different VLANs. Thus, broadcast messages are restricted to a VLAN.
VLAN has the following advantages
Restrict broadcast domains
Broadcast domains are restricted to a single VLAN, saving bandwidth and increasing network processing capability.
Enhance networking security
Messages in different VLANs are isolated during transmission, i.e., users in one VLAN cannot communicate directly with users in other VLANs.
Ensure networking reliability
Failures are restricted to one VLAN, which can not affect the operation of other VLANs.
High flexibility
VLAN divides different users into workgroups, and users in the same workgroup do not have to be limited to a fixed physical range, making network construction and maintenance more convenient and flexible.
VLAN vs. Subnet
Subnet and VLAN are two important concepts to understand when it comes to networking.
The subnet is a way of breaking up a larger-scale network into smaller, more scalable, and secure networks.
VLAN provides an additional layer of security by creating virtual networks within the same physical infrastructure.
Both two technologies can be used to segment traffic, enhance performance, and increase the overall security of your network. While subnet also helps to reduce the number of IP addresses needed for a particular network.
|
|
VLAN |
Subnet |
|
Difference |
Partition of the Layer 2 network. |
Partition of the Layer 3 network |
|
After the route interworking is implemented based on the configured VLANIF interface, users in different VLANs can only access each other. |
As long as the network is interoperable through routing, users in different subnets can access each other. |
|
|
It can divide into 4094 VLANs, and the number of devices in the VLAN is not limited. |
The number of segments divided affects the maximum number of devices in each subnet. |
|
|
Correlation |
It can divide multiple segments within the same VLAN. |
It can divide multiple VLANs within the same subnet |
VLAN Tag & VLAN ID
A piece of contained information must be in the VLAN tags to ensure the Ethernet switch identifies messages from different VLANs. And the IEEE 802.1Q is the protocol that adds a carried 4-byte VLAN tag in an Ethernet data frame between its Source/Destination MAC address and Length/Type fields.
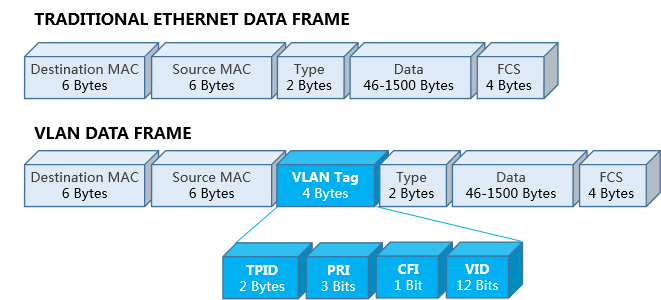
The VID in the data frame identifies the VLAN to which the frame belongs, and this frame can only be transmitted within its VLAN. The VID represents the VLAN ID, which takes values from 0 to 4095. Since 0 and 4095 are protocol reserved values, the valid range for the VLAN ID is 1 to 4094.
The data frames processed internally by the switch are tagged with VLAN tags, while some of the devices connected to the switch (e.g., hosts and servers) will only send and receive legacy Ethernet data frames without VLAN tags. That means if you want to access these devices, it requires the ability to recognize legacy Ethernet data frames on interfaces of the switches. At the same time, the interfaces should support adding or deleting VLAN tags when frames are sent and received. What VLAN tag is added is determined by the default VLAN (Port Default VLAN ID (PVID)) on the interface.
Processing mechanisms on interface type and tag of VLAN
In a network, users in the same VLAN may connect to different switches, and there might be more than one VLAN across the network switches. Realizing the communication between those users requires the interfaces of switches to recognize and send data frames of multiple VLANs. Generally, it accommodates different connections and networking depending on the connected devices, the processing of sent and received data frames, and current multiple VLAN interface types.
There are three common definition of VLAN interface types, including: Access, Trunk and Hybrid.
Access Interface
The access interface is generally used to connect with user terminals (such as user hosts and servers) that cannot identify VLAN tags or when it is not necessary to identify between different VLAN members.
In a VLAN-switched network, Ethernet data frames take two forms, untagged and tagged.
The untagged frame is the raw frame without a 4-byte VLAN tag. In most cases, the access interface can only send and receive untagged frames and can only add a unique VLAN tag to untagged frames. Since the Ethernet switch only handles tagged frames internally, the access interface adds a VLAN Tag to the received data frames, namely configuring the default VLAN. Once the default VLAN is configured, it will add the access interface to the VLAN. Nevertheless, if the VID and PVID are the same in the tagged frame, the access interface can also receive and handle it. And the access interface strips the tag before sending the tagged frame.
Trunk Interface
Trunk interfaces are used to connect switches, routers, APs, and voice terminals that can send and receive both tagged and untagged frames. The trunk interfaces allow tagged frames from multiple VLANs to pass and send untagged frames belonging to the default VLAN. The trunk interface would mark the received untagged frames with the tag related to the default VLAN(Native VLAN).
Hybrid Interface
The Hybrid interface can be used to connect both user terminals (e.g., user hosts, servers) and network devices (e.g., Hubs) that are not Tag-aware, as well as switches, routers, and voice terminals, APs that can send and receive both Tagged and Untagged frames. It can be configured to allow frames from certain VLANs with Tag (i.e., no Tag stripping) and frames from certain VLANs without Tag (i.e., Tag stripping) as needed.
It must use hybrid interfaces in some applications. For example, in the flexible QinQ, messages from multiple VLANs in the service provider's network need to be stripped of their outer VLAN Tag before entering the subscriber's network. And the trunk interface cannot complete this function because the Trunk interface can only allow messages from the interface's default VLAN to pass without the VLAN Tag.
Application of VLAN
Common usage scenarios for VLANs include Layer 2 isolation of users between VLANs, and Layer 3 inter-access for users between VLANs.
Layer 2 isolation of users between VLANs
As shown in the figure below, there are several companies in a business building. In order to reduce costs, several companies share network resources, and each company is connected to different interfaces of a Layer 2 switch and accesses the Internet through a unified exit.
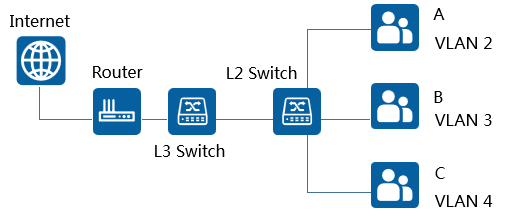
In order to ensure the independence and security of each company's business, the interfaces connected by each company can be divided into different VLANs to achieve complete isolation of business data between companies. It can be considered that each company has an independent "virtual router", and each VLAN is a "virtual workgroup".
Another example is that a company has two departments, each assigned a fixed IP network segment. In order to enhance learning and communication between employees, the locations of employees are sometimes transferred to each other, but the company hopes that the network resources accessed by employees in each department will remain unchanged.
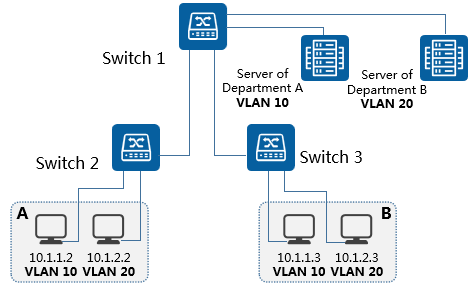
To ensure that the access to network resources remains unchanged after the location of employees within the department is adjusted, VLANs based on IP subnets can be configured on the company's switch Switch_1. In this way, different network segments of the server are divided into different VLANs, and the data flow to access different application services of the server is isolated, improving security.
Layer 3 inter-access for users between VLANs
The two departments of the company are connected to a layer 3 switch through layer 2 switches, belonging to VLAN2 and VLAN3 respectively.

You can divide VLANs on Switch 1 and Switch 2 and pass the VLANs through to Switch 3, then configure a VLANIF interface for each VLAN on Switch 3 to achieve routing between VLAN2 and VLAN3.
Protocols related to VLAN
IEEE 802.1Q
IEEE 802.1Q (also known as Dot1q), the Virtual Bridged Local Area Networks protocol, specifies the standard for VLAN implementation. Compared to the standard Ethernet data frame, it contains a 4-byte VLAN tag in the VLAN data frame.
LNP
Link-type Negotiation Protocol (LNP) is used to dynamically negotiate the link type of an Ethernet interface as Access or Trunk.
- The link-type negotiation for an Ethernet interface is Access, which is added to VLAN 1 by default.
- The link type of the Ethernet interface is negotiated as Trunk, which is added to VLANs 1 to 4094 by default.
QinQ
QinQ (802.1Q-in-802.1Q) protocol is from IEEE 802.1ad standard protocol, which can extend the VLAN space by adding another layer of 802.1Q Tag on top of 802.1Q tagged messages so that the private VLAN can pass through the public network
QinQ (802.1Q-in-802.1Q) protocol is from IEEE 802.1ad standard protocol, which can extend the VLAN space by adding another layer of 802.1Q Tag on top of 802.1Q tagged messages so that the pri
Problems with VLAN in cloud-based scenarios
With the development of network technology, cloud computing has become the new trend of enterprise IT construction nowadays by its advantages in high system utilization, low labor and management costs, flexibility, and scalability. And server virtualization, as one of the core technologies of cloud computing, has been increasingly applied.
As a traditional network isolation technology, the number of VLANs in the standard definition is only 4096, which cannot meet the demand for inter-tenant isolation in large data centers. In addition, the Layer 2 range of VLANs is generally small and fixed, which cannot support the dynamic migration of virtual machines on a large scale.
Therefore, the RFC defines the VLAN extension scheme VXLAN (Virtual eXtensible Local Area Network), which uses MAC in UDP (User Datagram Protocol) encapsulation and is a network virtualization technology in NVO3 (Network Virtualization over Layer 3). VXLAN perfectly compensates for the above-mentioned shortcomings of VLAN. On the one hand, it provides the identification capability of up to 16M tenants through the 24-bit VNI (VXLAN Network Identifier) field in VXLAN, which is much larger than the number of VLANs; on the other hand, VXLAN essentially provides the identification capability of up to 16M tenants through the 24-bit VNI (VXLAN Network Identifier) field in VXLAN, which is much larger than the number of VLANs; On the other hand, VXLAN essentially builds a virtual tunnel between two switches across the data center's underlying IP network, virtualizing the data center network into a giant "Layer 2 switch" to meet the needs of dynamic migration of virtual machines on a large scale.
+86-755-83898016-863
+86-1501-2669-765
[email protected]
Note: To speed up our service to you, please make sure the field with " * " mark is filled before you click on "Submit" button, Thank you!